HIPAA Security Rule Standards
The HIPAA Security Rule identifies standards and implementation specifications that organizations must meet in order to become compliant. All organizations, except small health plans, that access, store, maintain or transmit patient-identifiable information are required by law to meet the HIPAA Security Standards by April 21, 2005. Small health plans have until 2006. Failing to comply can result in severe civil and criminal penalties.
The general requirements of the HIPAA Security Rule establish that covered entities must do the following:
- Ensure the confidentiality, integrity, and availability of all electronic protected health information (ePHI) the covered entity creates, receives, maintains, or transmits.
- Protect against any reasonably anticipated threats or hazards to the security or integrity of such information.
- Protect against any reasonably anticipated uses or disclosures of such information that are not permitted or required.
- Ensure compliance by the workforce.
Covered entities have been provided flexibility of approach. This implies:
- Covered entities may use any security measures that allow the covered entity to reasonably and appropriately implement the standards and implementation specifications.
In deciding which security measures to use, a covered entity must take into account the following factors:
- The size, complexity, and capabilities of the covered entity.
- The covered entity’s technical infrastructure, hardware, and software security capabilities.
- The costs of security measures.
- The probability and criticality of potential risks to electronic protected health information.
Figure 1 CIA of ePHI
The core objective of the HIPAA Security Rule is for all covered entities such as pharmacies, hospitals, health care providers, clearing houses and health plans to support the Confidentiality, Integrity and Availability (CIA) of all ePHI.
The core objective is for organizations to support the CIA of all ePHI. Figure illustrates this point.
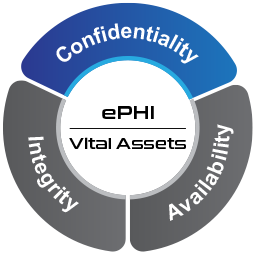
The HIPAA Security Rule outlines the requirements in five major sections:
- Administrative Safeguards
- Physical Safeguards
- Technical Safeguards
- Organizational Requirements
- Policies, Procedures and Documentation Requirements
Figure 2 Privacy Rule and Security Rule Safeguard requirements
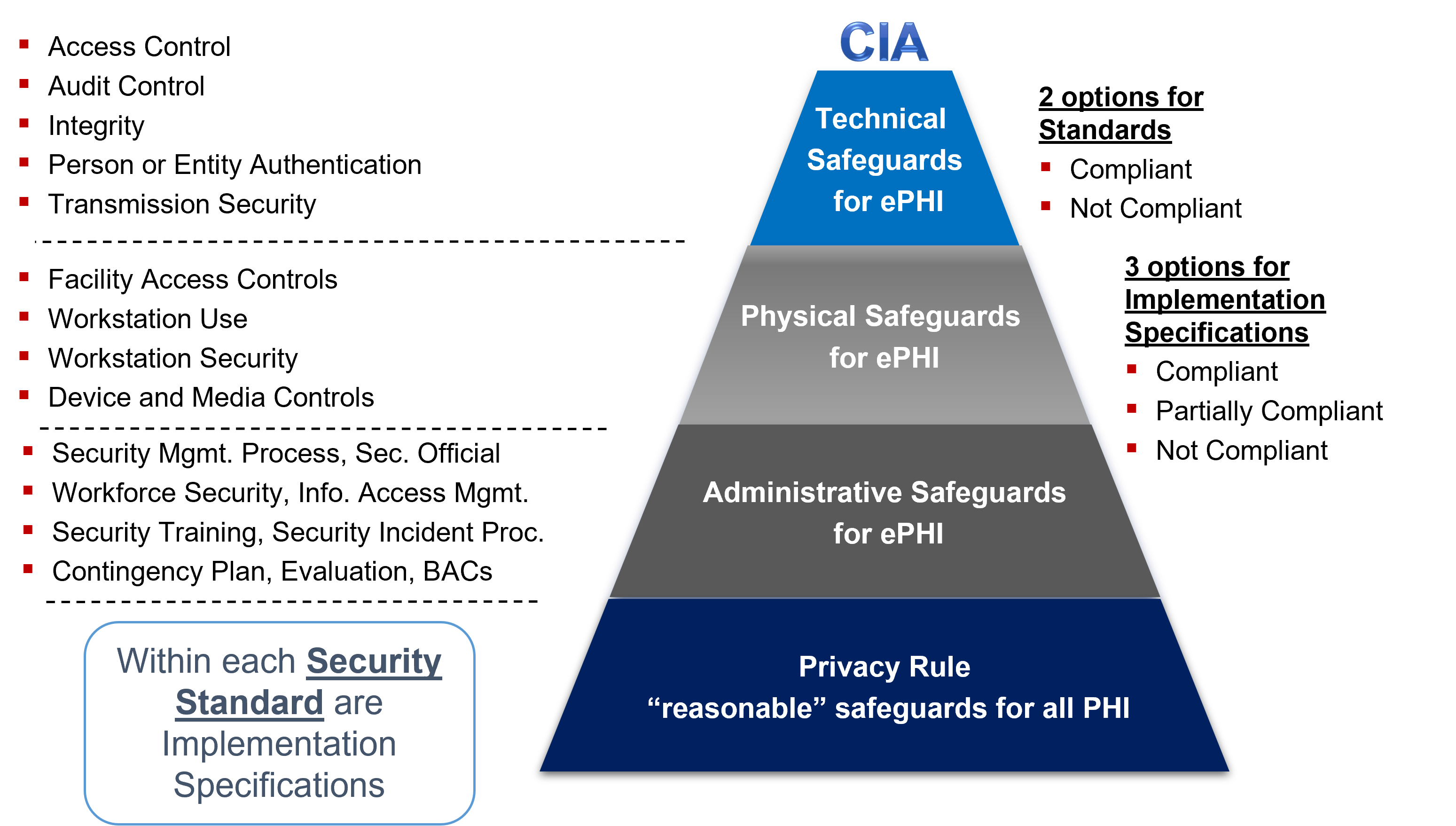
Figure 3: Administrative Safeguards Standards.
Administrative safeguards are administrative actions, and policies and procedures, to manage the selection, development, implementation, and maintenance of security measures to protect ePHI and to manage the conduct of the covered entity’s workforce in relation to the protection of that information. Figure 3 summarizes the Administrative Safeguards’ standards and their associated required and addressable implementation specifications.
|
Standards
|
Implementation Specifications
|
R = Required
A = Addressable |
| Security Management Process | Risk Analysis |
R
|
| Risk Management |
R
|
|
| Sanction Policy |
R
|
|
| Information System Activity Review |
R
|
|
| Assigned Security Responsibility |
R
|
|
| Workforce Security | Authorization and/or Supervision |
A
|
| Workforce Clearance Procedure |
A
|
|
| Termination Procedures |
A
|
|
| Information Access Management | Isolating Health care Clearinghouse Function |
R
|
| Access Authorization |
A
|
|
| Access Establishment and Modification |
A
|
|
| Security Awareness and Training | Security Reminders |
A
|
| Protection from Malicious Software |
A
|
|
| Log-in Monitoring |
A
|
|
| Password Management |
A
|
|
| Security Incident Procedures | Response and Reporting |
R
|
| Contingency Plan | Data Backup Plan |
R
|
| Disaster Recovery Plan |
R
|
|
| Emergency Mode Operation Plan |
R
|
|
| Testing and Revision Procedure |
A
|
|
| Applications and Data Criticality Analysis |
A
|
|
| Evaluation |
R
|
|
| Business Associate Contracts and Other Arrangement | Written Contract or Other Arrangement |
R
|
Figure 4: Physical Safeguards Standards.
Physical safeguards are physical measures, policies, and procedures to protect a covered entity’s electronic information systems and related buildings and equipment, from natural and environmental hazards, and unauthorized intrusion. Figure 4 summarizes the Physical Safeguards’ standards and their associated required and addressable implementation specifications.
|
Standards
|
Implementation Specifications
|
R = Required
A = Addressable |
| Facility Access Controls | Contingency Operations |
A
|
| Facility Security Plan |
A
|
|
| Access Control and Validation Procedures |
A
|
|
| Maintenance Records |
A
|
|
| Workstation Use |
R
|
|
| Workstation Security |
R
|
|
| Device and Media Controls | Disposal |
R
|
| Media Re-use |
R
|
|
| Accountability |
A
|
|
| Data Backup and Storage |
A
|
Figure 5: Technical Safeguards Standards
Technical safeguards refer to the technology and the policy and procedures for its use that protect electronic PHI and control access to it. Figure 5 summarizes the Technical Safeguards’ standards and their associated required and addressable implementation specifications.
|
Standards
|
Implementation Specifications
|
R = Required
A = Addressable |
| Access Control | Unique User Identification |
R
|
| Emergency Access Procedure |
R
|
|
| Automatic Logoff |
A
|
|
| Encryption and Decryption |
A
|
|
| Audit Controls |
R
|
|
| Integrity | Mechanism to Authenticate Electronic PHI |
A
|
| Person or Entity Authentication |
R
|
|
| Transmission Security | Integrity Controls |
A
|
| Encryption |
A
|
The Organizational Requirements section of the HIPAA Security Rule includes the Standard, Business associate contracts or other arrangements. A covered entity is not in compliance with the standard if the it knows of a pattern of an activity or practice of the business associate that constitutes a material breach or violation of the business associate’s obligation to safeguard ePHI (under the contract or other arrangement), unless the covered entity takes reasonable steps to cure the breach or end the violation, as applicable. If such steps are unsuccessful, the covered entity is required to:
Terminate the contract or arrangement, if feasible or
If termination is not feasible, report the problem to the Secretary (HHS).
The required implementation specifications associated with this standard are:
- Business Associate Contracts
- Other Arrangements
- Policies, Procedures and Documentation Requirements (164.316)
The Policies, Procedures and Documentation requirements includes two standards:
- Policies and Procedures Standard
- Documentation Standard
A covered entity must implement reasonable and appropriate policies and procedures to comply with the standards and implementation specifications. This standard is not to be construed to permit or excuse an action that violates any other standard, implementation specification, or other requirement. A covered entity may change its policies and procedures at any time, provided that the changes are documented and are implemented in accordance with this subpart.
A covered entity must maintain the policies and procedures implemented to comply with this subpart in written (which may be electronic) form. If an action, activity or assessment is required to be documented, the covered entity must maintain a written (which may be electronic) record of the action, activity, or assessment.
Business Associates
Similar to the Privacy Rule requirement, covered entities must enter into a contract or other arrangement with business associates.
The contract must require the business associate to:
- Implement safeguards that reasonably and appropriately protect the confidentiality, integrity, and availability of the electronic protected health information that it creates, receives, maintains, or transmits;
- Ensure that any agent, including a subcontractor, to whom it provides this information agrees to implement reasonable and appropriate safeguards;
- Report to the covered entity any security incident of which it becomes aware;
- Make its policies and procedures, and documentation required by the Security Rule relating to such safeguards, available to the Secretary for purposes of determining the covered entity’s compliance with the regulations; and Authorize termination of the contract by the covered entity if the covered entity determines that the business associate has violated a material term of the contract.
The regulations contain certain exemptions to the above rules when both the covered entity and the business associate are governmental entities. This includes deferring to existing law and regulations, and allowing the two organizations to enter into a memorandum of understanding, rather than a contract, that contains terms that accomplish the objectives of the business associate contract.
Preemption
Generally, the Security Rule preempts contrary state law, except for exception determinations made by the Secretary.
Enforcement
Enforcement of the Security Rule is the responsibility of CMS. However, enforcement regulations will be published in a separate rule, which is forthcoming.
For more information about HIPAA Academy’s consulting services, please contact ecfirst.