- Services
- HIPAA & HITECH Risk Analysis
- Business Impact Analysis & Disaster Recovery
- HIPAA & HITECH Vulnerability Assessment
- Health IT Services

HIPAA & HITECH Require Risk Analysis
A key requirement of the HIPAA and HITECH regulations is that covered entities and business associates must conduct a comprehensive and thorough assessment of the potential risks and vulnerabilities to the Confidentiality, Integrity, and Availability (CIA) of all electronic Protected Health Information (EPHI). These HIPAA and HITECH mandates require that organizations must complete a comprehensive and thorough vulnerability assessment on a regular schedule.
OCR Guidance on HIPAA Risk Analysis
The guidance published by the Office of Civil Rights states that, “Conducting a risk analysis is the first step in identifying and implementing safeguards that comply with and carry out the standards and implementation specifications in the Security Rule. Therefore, a risk analysis is foundational…”. Further, OCR states that, “All EPHI created, received, maintained or transmitted by an organization is subject to the Security Rule. The Security Rule requires entities to evaluate risks and vulnerabilities in their environments and to implement reasonable and appropriate security measures to protect against reasonably anticipated threats or hazards to the security or integrity of EPHI. Risk analysis is the first step in that process.”
ecfirst’s bizSHIELDtm program satisfies this HIPAA requirement.
HITECH Meaningful Use Requirements Include Risk Analysis
Demonstrating Meaningful Use of an Electronic Health Record (EHR) requirement tells organizations that they must, “Implement systems to protect the privacy and security of patient data.” Organizations seeking to demonstrate Meaningful Use must, “Conduct or review a security risk analysis and implement security updates as necessary, and correct identified security deficiencies.”
ecfirst’s bizSHIELDtm program satisfies this HITECH requirement.

Hospitals, health systems, physician practices, payers such as insurance organizations, as well as business associates must conduct a comprehensive risk analysis exercise to meet HIPAA mandates, including HITECH Meaningful Use requirements for Stage 1.
Have you completed a risk analysis exercise recently? ecfirst, Home of The HIPAA Academy™, can address this mandate now.
HIPAA & HITECH Require Risk Analysis
A key requirement of the HIPAA and HITECH regulations is that covered entities and business associates must conduct a comprehensive and thorough assessment of the potential risks and vulnerabilities to the Confidentiality, Integrity, and Availability (CIA) of all electronic Protected Health Information (EPHI). These HIPAA and HITECH mandates require that organizations must complete a comprehensive and thorough vulnerability assessment on a regular schedule.
OCR Guidance on HIPAA Risk Analysis
The guidance published by the Office of Civil Rights states that, “Conducting a risk analysis is the first step in identifying and implementing safeguards that comply with and carry out the standards and implementation specifications in the Security Rule. Therefore, a risk analysis is foundational…”. Further, OCR states that, “All EPHI created, received, maintained or transmitted by an organization is subject to the Security Rule. The Security Rule requires entities to evaluate risks and vulnerabilities in their environments and to implement reasonable and appropriate security measures to protect against reasonably anticipated threats or hazards to the security or integrity of EPHI. Risk analysis is the first step in that process.”
ecfirst’s bizSHIELDtm program satisfies this HIPAA requirement.
HITECH Meaningful Use Requirements Include Risk Analysis
Demonstrating Meaningful Use of an Electronic Health Record (EHR) requirement tells organizations that they must, “Implement systems to protect the privacy and security of patient data.” Organizations seeking to demonstrate Meaningful Use must, “Conduct or review a security risk analysis and implement security updates as necessary, and correct identified security deficiencies.”
ecfirst’s bizSHIELDtm program satisfies this HITECH requirement.
bizSHIELDtm – An ecfirst Risk Analysis Service
ecfirst developed the bizSHIELDtm program to assist Covered Entities, Business Associates, and vendors of Electronic Health Records (EHRs) and Personal Health Records (PHRs) in meeting the requirements of the HIPAA Privacy and Security Rule, The HITECH Act, and all subsequent guidance documentation and settlement agreements.
As a part of the bizSHIELDtm program, ecfirst will list every requirement of the HIPAA Security Rule including every Safeguard, Standard, and Implementation Specification in a risk analysis format that identifies an organization’s state of compliance with the requirement, recommended remediation activity, and associated risk priority. All remediation activities will be listed according to recommended implementation time bands in the bizSHIELDtm Corrective Action Plan (CAP) table. The bizSHIELDtm report is an actionable, documented risk analysis that provides both in depth and executive summary level findings appropriate to all audiences from administrators to the Board of Directors.
Privacy Gap Assessment Service
bizSHIELDtm helps an organization to understand, improve, or verify their compliance with the HIPAA Privacy Rule. bizSHIELDtm provides both summary and detailed compliance information as well as all necessary remediation activities pertinent to the organization’s business model. bizSHIELDtm will enable an organization to quickly determine the state of compliance, needed remediation, and will list actionable steps to achieve compliance.
HITECH Data Breach Service
Under the HITECH Data Breach Rule, organizations are required to take steps to prevent, identify, report, and remediate data breaches of unsecured information. The ecfirst TRACER solution will document the ability of the organization to detect a breach, review the incident management policy and procedures, and make recommendations. In addition, organizations will receive a HITECH Data Breach policy and several Data Breach procedures to ensure compliance, should a breach happen.

Contingency planning, also referred to as Business Continuity Planning (BCP), is a coordinated strategy that involves plans, procedures and technical measures to enable the recovery of systems, operations, and data after a disruption. A Business Impact Analysis (BIA) is the foundation for building Contingency Plans.
Once the BIA is completed, Contingency Plans can be developed using the information identified in the BIA. Typically, two types of Contingency Plans will need to be developed. Emergency Mode Plans for business unit recovery and Disaster Recovery Plans (DRP) for Information Technology (IT) systems and infrastructures.
HIPAA Compliance Mandates
Contingency plan is a HIPAA Security standard. The objective of the contingency plan standard is to establish (and implement as needed) policies and procedures for responding to an emergency or other occurrence (for example, fire, vandalism, system failure, and natural disaster) that damages systems that contain EPHI. As shown in bold in the Figure below, the Contingency Plan standard is defined within the Administrative Safeguards section of the HIPAA Security Rule.
| Standards | Implementation Specifications | R=Required A=Addressable |
| Contingency Plan | Data Backup Plan Disaster Recovery Plan Emergency Mode Operation Plan Testing and Revision Procedure Applications and Data Criticality Analysis |
R R R A A |
Contingency plan related requirements are also identified as implementation specifications in the Physical Safeguards section of the HIPAA Rule as well as the Technical Safeguards section.
It Starts with a BIA
A BIA is a critical step in contingency planning. The critical steps for a BIA include the need to:
- Identify business disruption events and measure probabilities
- Identify critical business functions
- Identify critical computer resources that support key business functions
- Identify disruption impacts and allowable outage times
- Develop recovery priorities
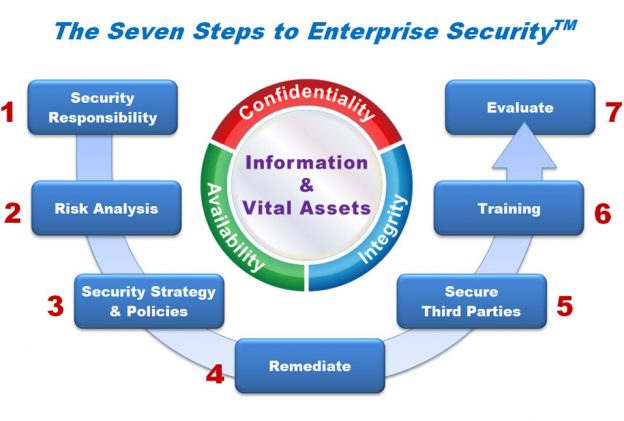
Our bizShieldtm Methodology
The Seven Steps to Enterprise Security™ is a methodology that describes a road-map to safeguard sensitive business information and enterprise vital assets. This methodology is also referred to as bizSHIELDtm. bizSHIELDtm has also been influenced by the clauses (domains) defined in the ISO 27002 security standards as well as the CobIT and NIST security frameworks.
The bizSHIELDtm methodology delivers Confidentiality, Integrity and Availability (CIA) of your vital information and business assets. This methodology provides the blueprint for defending today’s enterprise. The Seven Steps methodology provides the framework for addressing contingency requirements.
The bizSHIELDtm security methodology identifies seven critical steps for an organization to follow as a twelve-month framework for organizing and prioritizing enterprise security initiatives.
Our Professional Team
ecfirst only engages credentialed professionals for its BIA engagements. Credentials such as CISSP, CSCS™ and CBCP are typical of ecfirst teams assigned to client engagements.Your Commitment to Us
- Interviews with key members of IT staff, key individuals in departments and management.
- Copies of IT system and network documentation including downtime procedures and inventory of vital assets such as servers and applications.
Our Deliverable to You
A bizSHIELDtm Business Impact Analysis (BIA) document will be created based on our review and analysis of information collected from your organization. This bizSHIELDtm Business Impact Analysis (BIA) Report will include information in the following areas:
- Business Risk Assessment
- Key business processes identification
- Time-bands for business service interruption management
- Financial and operational impact
- Key Sensitive Systems and Applications Summary
- Emergency Incident Assessment
- BIA process control summary for emergency incident assessment
- Serious information security incidents
- Environmental disasters
- Organized and/or deliberate disruption
- Loss of utilities and services
- Equipment or system failure
- Other emergency situations
Fixed Fee with a Monthly Payment Schedule: Call for details and a customized proposal exclusively for your organization. On-Demand Compliance Solutions from ecfirst provides your organization with access to specialized compliance and security skills with no short term or long term commitments. Get Started Today!
Complimentary Private Webcast on Contigency Planning & BIA
For a complimentary private Webcast on Contingency Planning & BIA, please contact Kris Laidley at +1.515.987.4044 ext 25 or Kris.Laidley@ecfirst.com..

Hospitals, health systems, physician practices, payers such as insurance organizations, as well as business associates must conduct a comprehensive technical vulnerability assessment exercise to meet HIPAA mandates, including HITECH Meaningful Use requirements for Stage1.
Have you completed a technical vulnerability assessment exercise recently? ecfirst, Home of The HIPAA Academy™, can address this mandate now.
A key requirement of the HIPAA and HITECH regulations is that covered entities and business associates must conduct a comprehensive and thorough assessment of the potentials risks and vulnerabilities to the Confidentiality, Integrity, and Availability (CIA) of all electronic Protected Health Information (EPHI). These HIPAA and HITECH mandates require that organizations must complete a comprehensive and thorough vulnerability assessment on a regular schedule.
bizSHIELDtm – An ecfirst Technical Vulnerability Assessment Service
ecfirst developed the bizSHIELDtm program to assist Covered Entities, Business Associates, and vendors of Electronic Health Records (EHRs) and Personal Health Records (PHRs) in meeting the requirements of the HIPAA Privacy and Security Rule, The HITECH Act, and all subsequent guidance documentation and settlement agreements.
As a part of the bizSHIELDtm program, ecfirst will list every requirement of the HIPAA Security Rule including every Safeguard, Standard, and Implementation Specification in a risk analysis format that identifies an organization’s state of compliance with the requirement, recommended remediation activity, and associated risk priority. All remediation activities will be listed according to recommended implementation time bands in the bizSHIELDtm Corrective Action Plan (CAP) table. The bizSHIELDtm report is an actionable, documented risk analysis that provides both in depth and executive summary level findings appropriate to all audiences from administrators to the Board of Directors.
Technical Vulnerability Assessment Service
The Office of Civil Rights (OCR) wants to ensure that organizations have identified all of the risks and vulnerabilities to the EPHI that they collect, store, process, or transmit. The ecfirst bizSHIELDtm risk analysis program includes a technical vulnerability assessment to address HIPAA and HITECH mandates with the objective of establishing and prioritizing compliance and security gaps.
The ecfirst bizSHIELDtm Technical Vulnerability Assessment Service supports several distinct components, including:- External Assessment
- Internal Assessment
- Firewall Assessment
- Wireless Assessment
- Social Engineering Assessment
- Penetration Testing (Express)
When was the last time your organization conducted a risk analysis activity that included a technical vulnerability assessment?
External Vulnerability Assessment
ecfirst will identify vulnerabilities within client’s Internet-facing infrastructure, and attached network systems. The ecfirst testing will analyze client externally accessible servers. Additional IP addresses can be assessed as required.
It is recommended that the testing include the following types of systems:
- E-commerce servers
- Internet or DMZ located Database servers
- Internet screening routers
- Internet-facing firewalls
- E-mail server
- DNS servers
- Servers storing or processing EPHI
- Web Applications
- Other sensitive systems
Internal Vulnerability Assessment
ecfirst will perform an internal network vulnerability assessment on client internal network infrastructure. This testing will verify that the security controls implemented on a sample set of five (5) selected hosts, including servers located in the IT Data Center or desktop PC images and provide an adequate level of protection against network attacks.
The Internal Network Assessment addresses the following areas:
- Active Directory
- Review Identity and Access Management
- Review passwords in use for complexity
- Endpoint data loss
- Review the number of removable mass storage and communication devices connected to company systems
- SNMP settings
- Identify systems that respond to default or easy to guess SNMP Community strings
- SQL servers
- Identify servers with SQL services listening that allow connections from any host
- Identify SQL services utilizing default or easy to guess credentials
- Networked systems
- Identify vulnerabilities and configuration issues
Firewall Assessment
ecfirst will review the organization’s Internet-facing firewall to identify the current security posture in three critical areas:
- Rulebase configuration
- Current IOS (or other operating system) and patch revision release level
- Vulnerability assessment of configuration file
Rulebase configuration is critical to the integrity and operating security of a firewall. The rulebase should be tied to business requirements. Every rule that is configured on a firewall is essentially a permissible security hole into the company’s network infrastructure. Each of these rules should have a well defined business need for existing. However, many corporations open rules for testing and never close them when the test has completed. Additionally, many rules are opened up because of then-current business needs, but never closed or repaired once that need, or the corresponding business contract, has ended. This results in legacy access and a vulnerability providing a pathway into the internal network.
Wireless Assessment
Wireless networks are particularly vulnerable to attacks because it is extremely difficult to prevent physical access to them. The only advantage they have in this respect is that an attacker must be in relative physical proximity to the network, which can limit the pool of potential attackers. However, with the price of high gain antennas being extremely small, attackers can strike from much further distances with affordable ease. To secure a wireless network, an administrator should know what types of vulnerabilities exist and what types of attacks can exploit them.
During the wireless assessment, ecfirst addresses the following areas:
- ecfirst will perform a wireless assessment at one location
- Discovering the Wireless Access Points visible within the location
- Identify potentially rogue devices – Rogue access points installed by employees without IT departmental consent
- Determine the existing WiFi Security Infrastructure such as SSID protection; MAC filtering, VPN and encryption mechanism used (if any), and possibly supplicant certificates
- Attempt to compromise wireless security after sniffing sufficient packets or performing man-in-the-middle attacks
Social Engineering Assessment
Organizations with excellent security programs often spend large amounts of money on capital purchases to implement technical security controls. However, employees or contractors of the entity often prove to be the weak link in the security chain. Employee and contractor education is a key component to any information security program. Authorized members of the workforce have both authenticated access to information systems as well as physical access to facilities and secured areas.
During the social engineering assessment, ecfirst will attempt to gain unauthorized or inappropriate access to facilities, secured areas, documents, credentials, or confidential data. ecfirst security personnel will attempt to bypass security controls that are in-place in order to gain access to various assets. ecfirst will attempt to bypass electronic, personnel, and procedural controls during this assessment. ecfirst will document and present a very detailed record of successes, failures, controls bypassed, access achieved and information obtained during the assessment.
Penetration Testing (Express)
The ecfirst Express Penetration Test is less comprehensive than the full Penetration Test in scope as it only addresses external and internal technical vulnerabilities & threats; physical and personnel vulnerabilities and threats are not evaluated. A detailed technical Corrective Action Plan (CAP) is included in the bizSHIELDtm report to provide actionable directives for addressing the identified deficiencies.
- External Penetration
- Reconnaissance phase (including the Google Hacking Database), Web Applications and Networked Systems phases are all performed in 1 day
- The Internal Penetration (including the Wireless Penetration) is generally performed in 1 day during the onsite visit

The HIPAA Academy™ offers the healthcare industry’s most flexible range of Health Information Technology (IT) services. What’s more is that the services are all based on flat rate pricing, that get even more valued based on the duration of service provided. The Health IT service options available now are:
- On-Demand Consulting
- Managed Compliance Services Program (MCSP)
On-Demand Consulting
You Can Do It, We Can Help! Starting with a commitment of 40-hours or more, you can secure IT professional resources with experience in the healthcare industry across a broad range of skill sets. So be with project management, security professionals, compliance professionals, system analysts, network engineers or more, talk to ecfirst about your requirements and how we can help with staffing or collaborating with you on your project initiatives under our management with your objectives.
We at ecfirst refer to this Health IT consulting model as – “you can do it, we can help!” ecfirst resources may be applied to work along with your personnel to help support, manage or implement IT solutions or capabilities. For example, ecfirst can support your activities with specialized resources such as:
- Project managers with experience as required
- Technical professionals with extensive technical, compliance or security expertise
The scope of work may be executed on-site, at your site, or offsite, as determined by your organization. Time-lines, reporting structure and frequency are mutually determined. A sampling of possible tasks and activities include:
- Develop and manage a Project Plan for IT project initiatives, such as Meaningful Use, or an EHR technology or application implementation
- Perform Project Management duties and provide technical implementation assistance
- Develop and manage policies to address proactive auditing
- Deploy systems, applications or technologies
- License assessment (software, application license audit)
- Develop a program, procedures, and logs to combine and filter audit logs, network activity review, and application security access reviews
- Assist in developing Incident Management capabilities, policy, and technical procedures
- Review solution options to encrypt sensitive information in e-mail or portable devices
Managed Compliance Services Program (MCSP)
We Get It Done! The Managed Compliance Services Program (MCSP) is the industry’s most unique and flexible managed services program. With the MCSP you decide what combination of services you contract with ecfirst to manage, and you determine the duration – one year, two years, three years or five years. The duration of the contract determines the flat rate discount you secure for the length of the contract.
And, to top it, payments are monthly for the duration of the contract, with absolutely no interest, and nothing due upfront!
So you decide what service components are to be delivered by ecfirst in what timeframe. It’s amazingly, simple!
For example, are your internal resources stretched to capacity and you lack the necessary expertise to identify all compliance gaps and security vulnerabilities? Does your organization need to comply with regulations and standards such as the HITECH Act, State Regulations, HIPAA Privacy and HIPAA Security?
Regulations mandate organizations to maintain compliance with reasonable and appropriate safeguards in several specific areas. Compliance requirements drive critical activities that must be conducted on a regular schedule, typically annually. On a regular schedule, organizations must by law:
- Assess compliance with the HIPAA, HITECH or State regulations
- Assign responsibility to the security officer who is responsible for coordinating compliance and security initiatives
- Conduct a comprehensive and thorough risk analysis including technical vulnerability assessment penetration testing)
- Complete a Business Impact Analysis (BIA) for contingency planning and disaster recovery
- Develop and update security policies and procedures
- Train all members of the workforce
- Audit the information infrastructure for compliance with the HIPAA Security Rule
Program Benefits
MCSP is designed to assist healthcare organizations and business associates manage compliance requirements, security and core components of the technology infrastructure. Key benefits of MCSP include:
- Clearly defined deliverables to achieve compliance
- Expert advisor assigned – serves as interim security advisor
- Activities such as risk analysis, technical vulnerability assessment and business impact analysis conducted on a regular schedule
- Policies maintained on a continual basis
- Easily tailored to your organizational requirements
- Very scalable program – can monitor and audit as required
- Skilled resource pool with expert domain knowledge
- Enables your staff to focus on your business and us on compliance
- Fixed monthly fee
- No interest
Further benefits of the MCSP include:
- A team of experts keeps you up to date on regulations
- We free up cycles to enable your staff to better focus on business-critical tasks
- In Depth resource capabilities with trusted knowledge of legislation and client infrastructure.
- Smooth out volatility in resource demands and costs associated with managing information technology
- ecfirst helps to minimize productivity losses from unexpected downtime
This chart summarizes key areas addressed by the ecfirst MCSP.
ecfirst’s Managed Compliance Services Program (MCSP)
The MCSP is designed to address your compliance, security and other technology implementation, support and management challenges. This program enables your organization to both lower costs and save time. The MCSP is a highly flexible and scalable service.
The MCSP provides a complete, end to end compliance service offering that can be tailored to meet your specific requirements.